# User Manual
| Document Version | Content Revision | Revised By | Revision Date |
|---|---|---|---|
| V1.0 | Initial Draft | Guochenghao | 2023-09-01 |
# Table of Contents
# Goals
- Address user difficulties: reduce usage costs
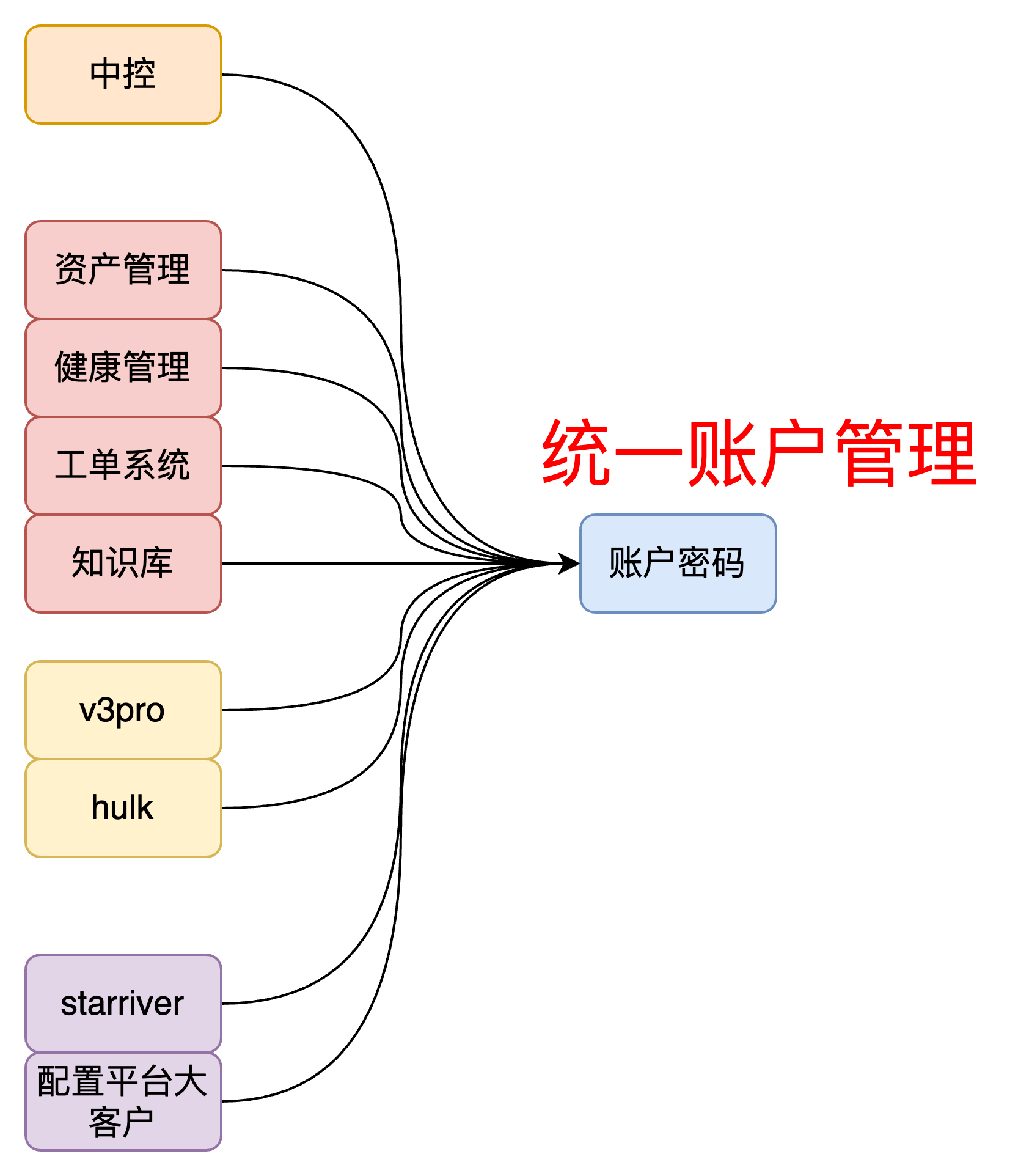
- Address the complexity of service integration: reduce interaction costs
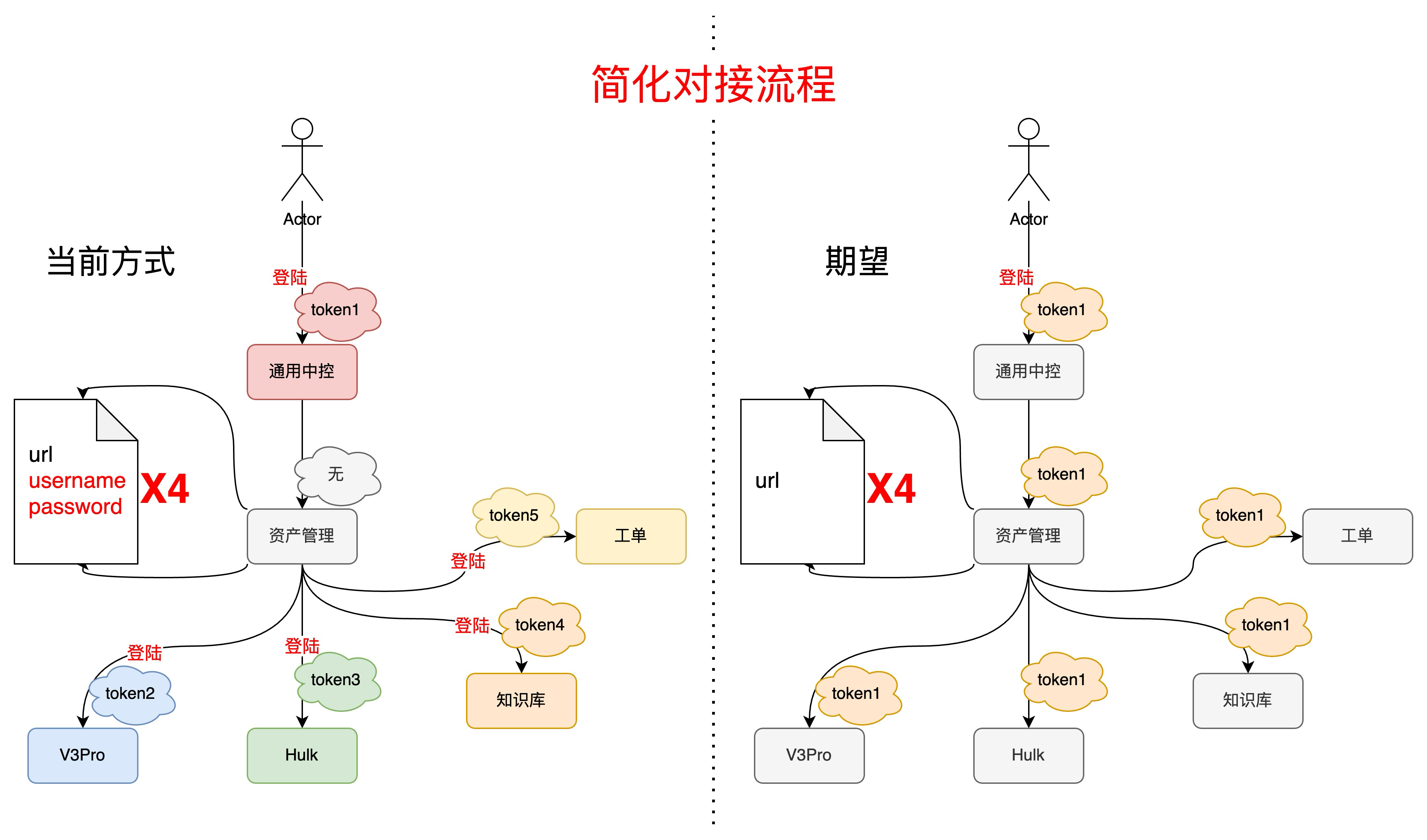
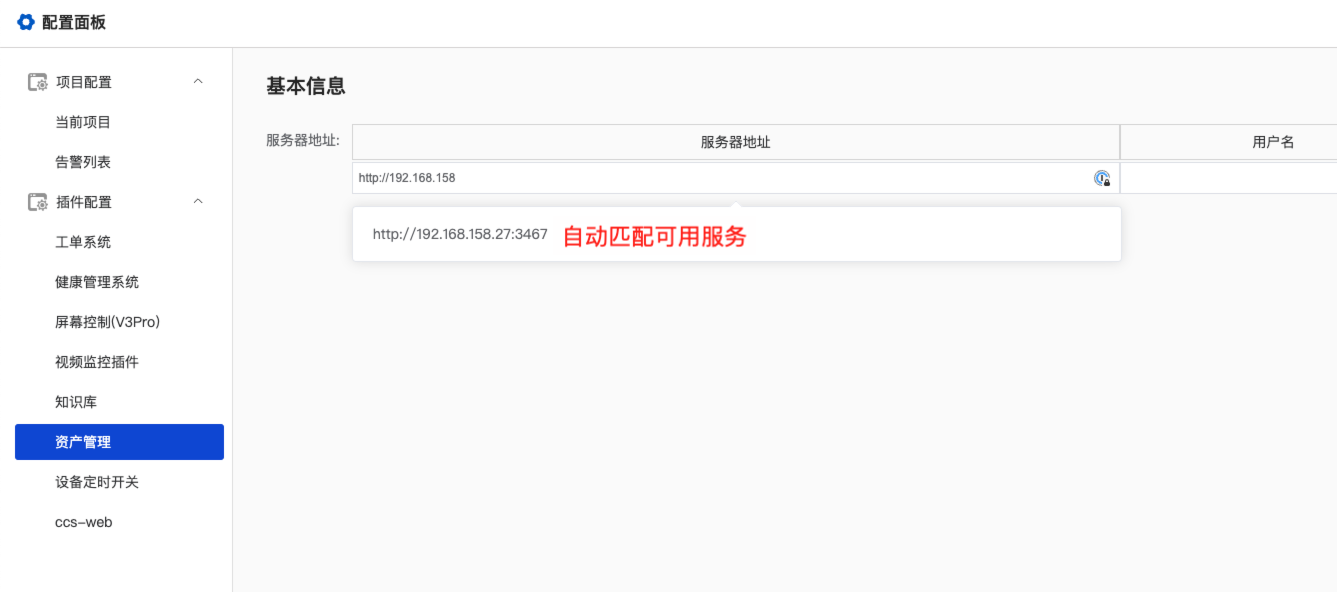
- Address the issue of excessive deployment configurations: reduce deployment costs
# Page Display
# Application List
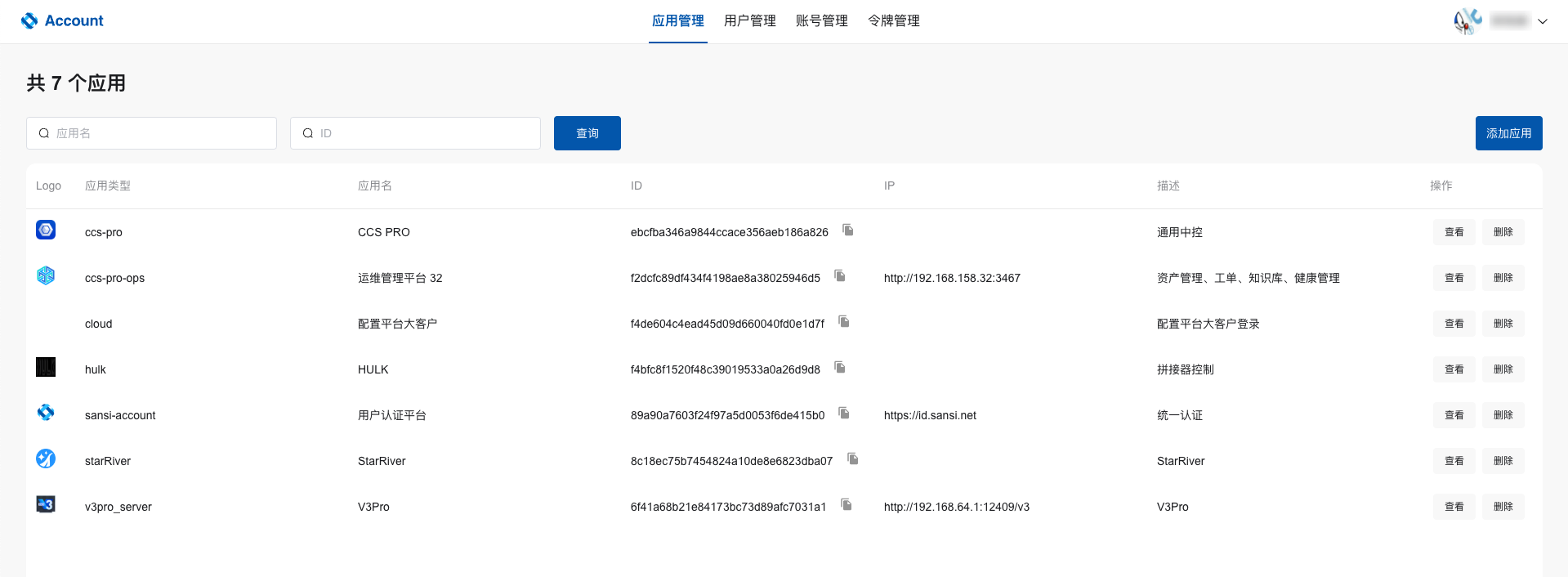
# User Management
# Personal Information
# Token Management
# Features
# Application Management
- View existing applications
- Search for available services on the local area network
- Edit application information
- Manage application roles
# User Management
- Add users
- Edit user information
- Set user enable/disable status
- Set user roles
# Account Management
- Maintain personal information
- Bind management accounts
# Token Management
- Add new tokens
- Delete tokens
# API
https://console-docs.apipost.cn/preview/1a52b8b93925675e/55922c519a517dd9
# Hardware and Operating System Requirements
| Hardware Requirements | Recommended Specifications |
|---|---|
| Processor (CPU) | >= i5-10500,arm or x84-64 |
| Memory(RAM) | >= 16G |
| Disk(DISK) | >= 512G,SSD recommended |
| Operating System | Recommended Version |
|---|---|
| Windows | >= Win10 |
| Macos | >= 12.1 |
| Ubuntu | >= 20.04 |
| Browser | Recommended Version |
|---|---|
| chrome | >= 90.0.4430 |
| edge | >= 90.0.818.8 |
# Authentication Process - Authorization Code Grant
+--------+ +---------------+
| |--(A)- Authorization Request ->| Resource |
| | | Owner |
| |<-(B)-- Authorization Grant ---| |
| | +---------------+
| |
| | +---------------+
| |--(C)-- Authorization Grant -->| Authorization |
| Client | | Server |
| |<-(D)----- Access Token -------| |
| | +---------------+
| |
| | +---------------+
| |--(E)----- Access Token ------>| Resource |
| | | Server |
| |<-(F)--- Protected Resource ---| |
+--------+ +---------------+
- A The client sends an authorization request to the resource owner;
- B The resource owner agrees to the client's authorization and returns an authorization code;
- C The client uses the authorization code to request a token from the authorization server;
- D The authorization server verifies the client's identity, and upon successful authentication, issues a token;
- E The client uses the issued token to request resources from the resource server;
- F The resource server verifies the token's validity and returns the resource information to the client.
# Authentication Process - Resource Owner Password Credentials Grant
+----------+
| Resource |
| Owner |
| |
+----------+
v
| Resource Owner
(A) Password Credentials
|
v
+---------+ +---------------+
| |>--(B)---- Resource Owner ------->| |
| | Password Credentials | Authorization |
| Client | | Server |
| |<--(C)---- Access Token ---------<| |
| | (w/ Optional Refresh Token) | |
+---------+ +---------------+
A The resource owner provides the username and password to the client.
B The client uses the username and password to request a token from the authorization server.
C The authorization server verifies the client and resource owner credentials, and if valid, returns the token.
# Service Discovery - Scope of Use
- Enabled on the local area network
- Disabled on the public network
If the service discovery feature is enabled, the application list page displays the service status field, and the list automatically refreshes every 5 seconds.
If the service discovery feature is disabled, the application list page does not display the service status field, and the list does not refresh automatically.
# Service Discovery - Principle
Uses SSDP to search for services. Upon discovering a service, the following actions are executed:
- Automatically search for available devices on the local area network.
If there are no services in application management, automatically create a new application.
If there are n services in application management, iterate through them to find the first service without a bound IP to auto-bind.
If there are n services in application management, and no bindable IP services are found, automatically create a new application.
- Application List
Unwanted services can be set to ignore.
Ignored applications can be restored to the application list by clicking 'Add Service - Ignored List' and then clicking 'Restore'.